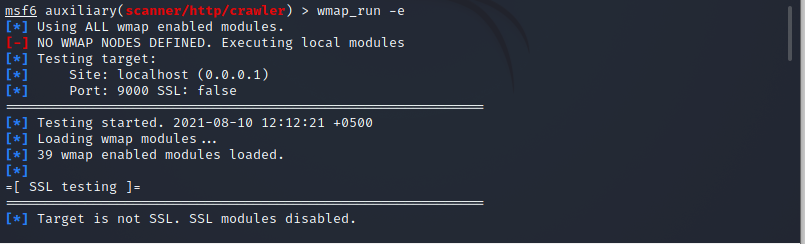
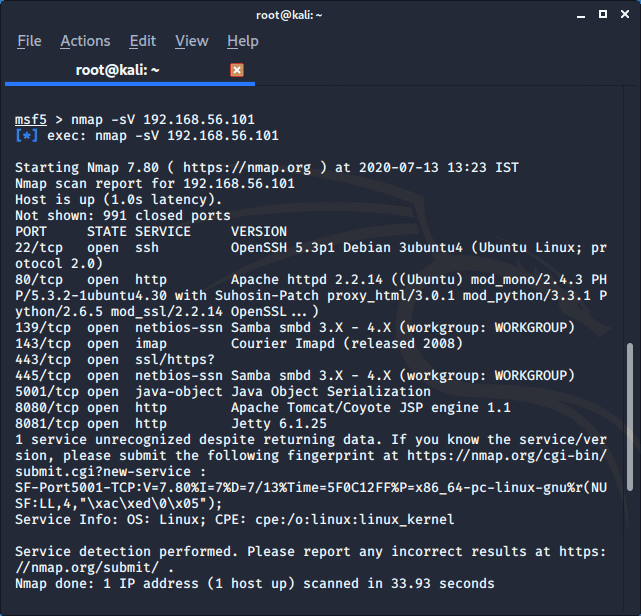
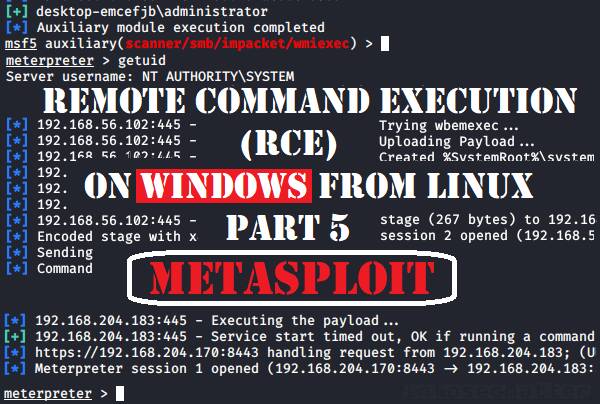
RAMELLA Sébastien on Twitter: "@shawn0x7e @metasploit @CERT_FR @zeop_officiel @Dinosn ~/.msf4/modules/auxiliary/scanner/http/apache_normalize_path.rb ~/modules/exploits/multi/http/apache_normalize_path_rce.rb You need both modules ... Run msfconsole ...

auxiliary/scanner/winrm/winrm_cmd: WinRM Authentication Issue (HTTP Error 500) · Issue #8900 · rapid7/metasploit-framework · GitHub
Total.js Directory Traversal. Metasploit framework is the most… | by Ashish Bhangale | Pentester Academy Blog
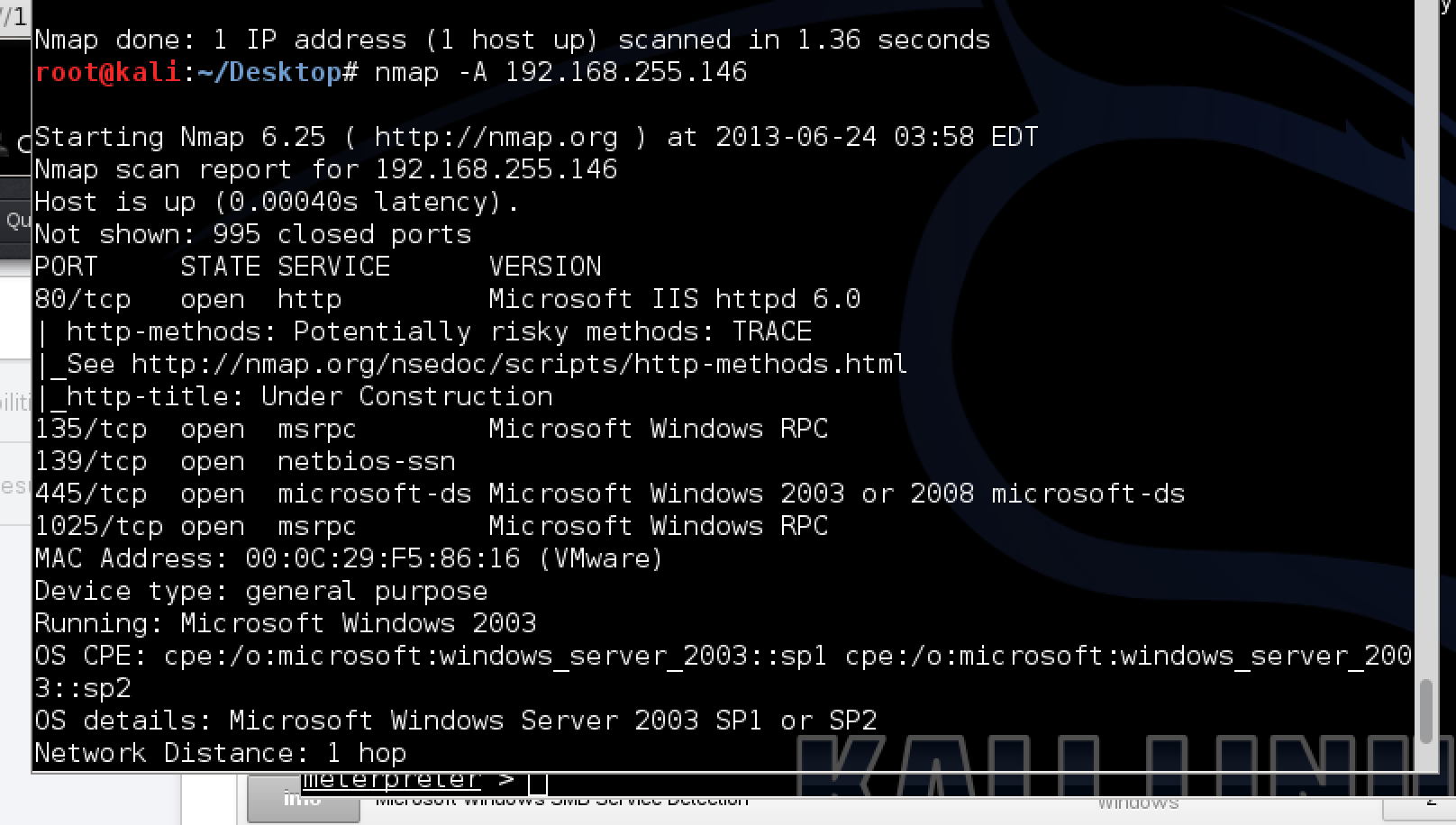
![Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book] Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book]](https://www.oreilly.com/api/v2/epubs/9781788624596/files/assets/15d23931-4396-4e2e-8b6e-6c4a90c7f021.jpg)


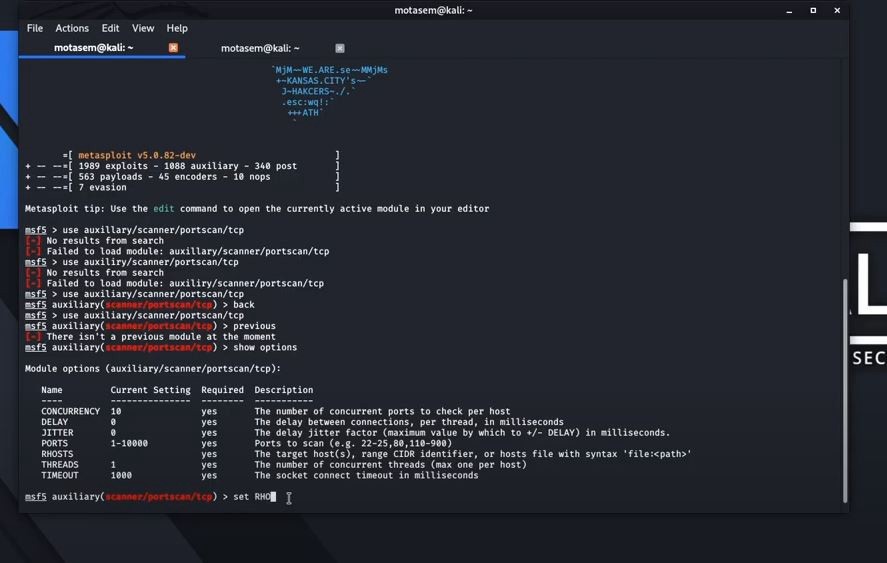
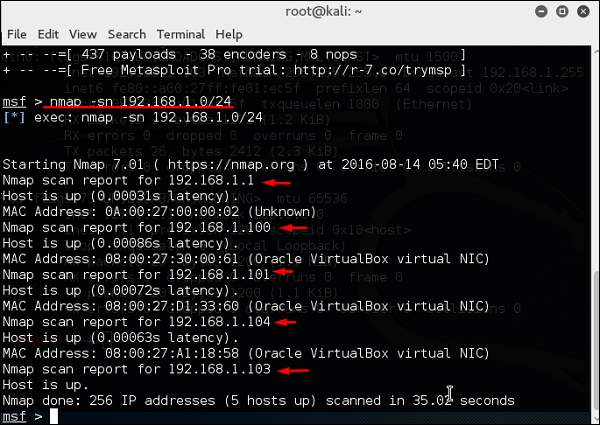
![UDP scanning with Metasploit - Kali Linux Network Scanning Cookbook - Second Edition [Book] UDP scanning with Metasploit - Kali Linux Network Scanning Cookbook - Second Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781787287907/files/assets/image103.jpg)